
 by Scott Jack
by Scott Jack
Content Contributor, E-N Computers
Over a decade of experience in technical support including end user support, mobile device management, application deployment, training, and documentation.
Updated March 5, 2025
Macro viruses—if you’ve been in IT for a few years, that term may have you thinking back to the ’90s. That’s when malicious code embedded in Office documents would do annoying, if not destructive, things — like sending itself to the first 50 people in your address book.
Believe it or not, Microsoft Office macros are still a serious security threat. Several of the recent Cryptolocker-type viruses, such as Locky, spread themselves through malicious Word macros. In those cases, the macro itself isn’t the virus. Once it’s activated, it executes a bit of Javascript that connects to a web server and downloads the virus payload.
By default, MS Word does not run macros automatically, but prompts the user to enable them if the document contains them. But virus writers have developed some sneaky social engineering tricks to get users to disable Protected Mode and run macros. For example, the malicious Word documents that spread the Locky virus appeared to have garbled formatting, strange characters, and gibberish, with a “helpful” note that said “If document is not formatted correctly, enable macros”.
So, unless macros are an important part of your company’s workflow, the safest option is to disable them completely using Group Policy. Disabling Microsoft Office macros is a quick and easy way to beef up your network security against new and emerging threats.
To disable macros in group policy, do the following:
QUICK ANSWER:
Why and how should I disable Office macros using Group Policy?
The people who write malware find sneaky ways to get users to turn off Protected mode and enable macros. Disabling macros in Group Policy blocks this attack vector. It’s easy as 1) create a policy, 2) set the policy to disable macros, and 3) test. More details below!
Set Up Group Policy
If you are already managing Office settings using Group Policy, you can skip this step. If not, you’ll need to import the MS Office administrative templates (ADMX files) for the version of Office that you’re using, and then create a new Group Policy Object to hold the macro settings.
Download the Administrative Templates for your version of Office from the Microsoft downloads site (for example, the files for Office 2021 can be found here.) Follow the instructions for importing ADMX templates into your central store here.
Then, open up Group Policy Management. Create a new group policy object in root of your domain. Name it something like “MS Office – Disable Macros”.
Disable Macros
Right-click and edit the GPO you just created (or your existing Office GPO). Navigate to User Configuration > Administrative Templates > Microsoft Word 20xx (where xx is your MS Office version) > Word Options > Security > Trust Center
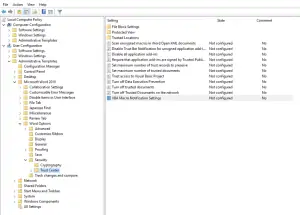
Double click on VBA Macro Notification Settings. Select “Enabled”, and change the dropdown to the setting you would like — “Disable All With Notification” is a good choice. Click OK.
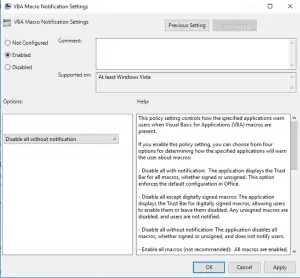
Repeat this step for each of the other Microsoft Office products (Excel, PowerPoint, and Outlook).
Test
Once you make these changes, run a gpupdate on a client workstation. Then, open Word, go to File > Options > Trust Center > Trust Center Settings > Macro Settings. You should see the macro setting that you set in the GPO selected, and the other options grayed out:
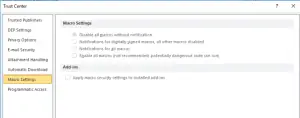
If that’s what you see, then you’re all set! You can rest easy knowing that your network is secure from one more potential security threat.
E-N Computers specializes in protecting organizations in Virginia, Maryland, and Washington, D.C. from all kinds of cyber threats.
Contact us today to find out how our managed IT services can keep you protected.
Modern examples of Office macro attacks
Despite Microsoft’s introduction of Protected View in 2010—fifteen years ago!—macro-based attacks continue to be a serious threat. Attackers have adapted by using more sophisticated social engineering tactics to convince users to enable macros. Here are just five macro-based attacks.
- Emotet Trojan: The CISA notice on Emotet, updated in 2020, mentions macro-based Word documents as a vector. In 2023, it was also found in OneNote attachments to bypass macro-blocking measures.
- Ransomware: In 2022, research conducted by Venafi and Forensic Pathways found that “87% of ransomware found on the dark web has been delivered by malicious macros.”
- TrickBot Trojan: TrickBot often infects systems via an Excel sheet with a malicious macro. After tricking users into enabling macros, can download additional malware, establish persistence on the system, and gain credential access. The TrickBot CISA advisory was last updated May 2021.
- Macro clusters: In September 2024, researchers discovered several new macro-infected documents created using a framework called MacroPack. These files could deliver multiple payloads, including the Havoc and Brute Ratel post-exploitation frameworks, and a new variant of the PhantomCore remote access trojan.
Disabling macros using Group Policy provides some protection, but a robust security suite and following the principle of least privilege are still critical. Microsoft Defender XDR provides protection in the Microsoft cloud and on endpoints so that threats are identified and remediated quickly. By following the principle of least privilege, you make sure that users do not have more rights than they need to do their work — nor excessive rights that can be taken advantage of by threat actors. Tools and policies like these can protect you against malware like Follina, a 2022 attack that exploited vulnerabilities to run malicious code with the user’s rights.
Next steps: Improve your IT security posture
READ: What is the best antivirus for business?
READ: How E-N Computers handles patch management
WATCH: Least privilege made simple with AutoElevate
CASE STUDY: Recovering after a ransomware attack
When you have the right people working together, you can implement systems and processes that actively help you reach your business goals. We sometimes call this IT maturity. But for many organizations, something is off when it comes to their partnerships, strategy, systems, and settings. How can you know what’s working well and where you have room for improvement? Start by taking our free IT Maturity Self-Assessment. You’ll walk away with some pointers and, if you want, a free appointment to discuss your results.
Not sure if you need managed IT services?
Take the IT Maturity Self-Assessment

In a few minutes, get actionable insights on your IT strategy, plus a free strategic consultation.

Industries
Locations
Waynesboro, VA
Corporate HQ
215 Fifth St.
Waynesboro, VA 22980
Sales: 540-217-6261
Service: 540-885-3129
Accounting: 540-217-6260
Fax: 703-935-2665
Washington D.C.
1126 11th ST. NW
Suite 603
Washington, DC 20001-4366
Sales: 202-888-2770
Service: 866-692-9082
VA DCJS # 11-6604
Locations
Harrisonburg, VA
45 Newman Ave.
Harrisonburg, VA 22801
Sales: 540-569-3465
Service: 866-692-9082
Richmond, VA
3026A W. Cary St.
Richmond, VA 23221
Sales: 804-729-8835
Service: 866-692-9082
