
 by Ian MacRae
by Ian MacRae
President and CEO, E-N Computers
25+ years experience solving business IT problems in Virginia and Washington, D.C.
Ian MacRae founded E-N Computers as an MSP in 1997. Today, the company is an MSSP and CMMC Registered Provider Organization. Ian is one of the CMMC Registered Practitioners at the company. He delivered this presentation at RVAsec in June 2023. This transcript is edited for clarity.
Why pay attention to NIST and CMMC? If you’re doing business with the federal government today, this is something that may already be on your radar. You may already be working on it.
Here in Virginia, doing business with the federal government is our number one business. We are number two only to California, which happens to be quite a big state, in terms of 12% of all federal procurement spent here.
I find it interesting that the Defense Industrial Base is comprised of over 100,000 businesses. To put that in perspective: that’s how many dentists there are. So there’s a lot of small mom and pop manufacturers out there that may not just be doing business with the federal government, but it might be their most stable client.
See the complete presentation video
QUICK ANSWER:
What is the state of NIST and CMMC compliance today?
NIST and CMMC are introducing much needed standards that affect both business policies and IT implementation. Most of what you’ll find in these frameworks are things that modern businesses should be doing anyway.
We currently expect the CMMC compliance requirement to appear in DoD contracts beginning in August 2024. Because a significant amount of time, effort, and resources are required to achieve CMMC compliance, you’re advised to work with a Registered Practitioner Organization like E-N Computers.
Table of Contents
- The need for information security standards
- The purpose of CMMC
- CUI marking
- Is my organization affected?
- Department of Defense DFARs rule
- Quick overview of the NIST 800-171 control families
- What is your SPRS score?
- CMMC compliance strategies
- CMMC assessment process
- What’s new with NIST 800-171 in 2023?
- Tips and tricks for achieving CMMC compliance
- Costs and pitfalls of seeking CMMC compliance
- Customer experiences in becoming CMMC compliant

The need for information security standards
Simply put, the government got sick of spending billions of dollars on intellectual property and finding that property in the hands of others. The Chinese J-31 seems like it’s a pretty close copy of the F-35. This is the type of stuff that really got the ire of lawmakers and got this CMMC compliance program stood up.
How did I get into this space? I got a call from good old Warren Buffet. Well, it was a manager of a manager — you know, way down the food chain — one of his subsidiaries that wanted to secure his factory, which happened to make parts for this gun among other things.
As I was working along their compliance journey back in 2017, I realized that I had grown up around my father as a building inspector. He taught me a love of architecture and also buildings. Other industries have standards; they have building codes. Whether you’re looking to build a house or fly a plane, there’s regulations there that you need to abide by to keep everybody safe.
What I felt in IT for a long time is that our industry had grown up during a period of profound deregulation. We don’t let people live in hovels, but IT closets are another thing. But without that architecture there, without a standard, security is pretty hard to achieve. So I resonated with the standards that the government was putting out. I didn’t see anything that was unreasonable. I saw many things that we had been advocating for for a long time.
Get the slide deck

Want the slides from Ian’s presentation? Enter your email address (totally optional!) and we’ll send you a link so you can download them later or share them with your team.
The purpose of CMMC
What is CMMC designed to protect? Let’s say you’re doing business with the federal government and you’re selling them socks. You’re looking to ship 10,000 socks to Guam.
A recent publication (archive link) said that our systems in Guam were being compromised by the Chinese because they might be interested in knowing if we’re coordinating troop movements to Guam to respond to something in Taiwan.
Obviously there’s no top secret information around socks. But if you’re selling socks or diesel fuel or any number of commodities, the federal government wants to keep some of this basic contract information, like the timing or location of the deliveries, private. This is called federal contracting information.
At this level, there’s a FARS clause. All government agencies have it. Here’s the law; it’s one of the more simple ones to read (emphasis ours).
Read the FARS clause
(1) The Contractor shall apply the following basic safeguarding requirements and procedures to protect covered contractor information systems. Requirements and procedures for basic safeguarding of covered contractor information systems shall include, at a minimum, the following security controls:
(i) Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
(ii) Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
(iii) Verify and control/limit connections to and use of external information systems.
(iv) Control information posted or processed on publicly accessible information systems.
(v) Identify information system users, processes acting on behalf of users, or devices.
(vi) Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational information systems.
(vii) Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
(viii) Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
(ix) Escort visitors and monitor visitor activity; maintain audit logs of physical access; and control and manage physical access devices.
(x) Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
(xi) Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks. (xii) Identify, report, and correct information and information system flaws in a timely manner.
(xiii) Provide protection from malicious code at appropriate locations within organizational information systems.
(xiv) Update malicious code protection mechanisms when new releases are available.
(xv) Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
(c) Subcontracts. The Contractor shall include the substance of this clause, including this paragraph (c), in subcontracts under this contract (including subcontracts for the acquisition of commercial products or commercial services, other than commercially available off-the-shelf items), in which the subcontractor may have Federal contract information residing in or transiting through its information system.
I put these up here for you to read because I hope you see in here that probably anybody in federal procurement – it could be a lawyer – could probably put this together. There’s nothing in here that’s all that crazy. And much of it we’ve been advocating for in IT for a long time. But it’s kind of hard to do without the buy-in of the business.
In a lot of businesses, you’re going to struggle with this even at the federal contracting level. This is the most basic level: things like having logs of visitors, making sure that systems are being monitored, basic stuff. It can be challenging.
So Federal Contracting Information (FCI) – this is Tier 1. This is CMMC Level 1 certification.
What if you’re looking at CMMC Level 2, (which is what I find most people are looking for)? Most people are having to meet an additional standard to store, process, and transmit Controlled Unclassified Information (CUI). And again, I’m going to put all of the things up here that are on the Archives Registry because even if you’re not doing business with the government today, you might see some things in here that you are doing business around or that your clients might be doing business in.
I don’t have any direct federal contracts. I got into this because I was an IT provider at Warren’s factory.
The CMMC compliance program is a DoD program. But look at all of the other areas of Controlled Unclassified Information. You have to be doing business with the government for CMMC to affect you. But maybe your client’s doing business with the government:
- critical infrastructure,
- defense,
- export control,
- financial, things like business valuations for publicly traded companies,
- immigration,
- intelligence,
- law enforcement,
- legal,
- natural resources,
- nuclear (the first class of CUI),
- privacy (PII),
- homeland security
- taxes: your local tax preparer isn’t being paid by the government, but we are seeing more regulations in this industry as well.
We’ve run into a lot of folks that are doing construction. And they’re in some of these trades because they’re concerned that our infrastructure is going to be compromised.
So there is free CUI security awareness training from the National Archives. Those are the same folks that are a little pissed off at Mr. Trump. They’re in charge of keeping track of all the government’s information.
CUI marking
If you are doing business with the government today — or if maybe you’re doing business with somebody who is doing business with the government, you’re their subcontractor and they’re the prime — there is often confusion around whether you’re actually dealing with one of these controlled and classified information categories. And it’s supposed to be marked.
According to the National Archives CUI Marking Handbook, it’s supposed to be marked “Controlled” or “CUI”. It’s supposed to be marked. Oftentimes it isn’t. Sometimes it is overmarked. I hear our customers saying, ‘Every email I get from these guys, even if they’re saying meet me at Taco Bell, says CUI at the top of it.’ It shouldn’t be that way.
One of the categories that I think is most difficult to deal with from an IT standpoint is export-controlled information. It can also be research information if you’re associated with a college or university that’s doing research. It’s mostly weapons systems that I’ve run into in Virginia, but this ITAR (International Traffic in Arms Regulations) has to be U.S. citizens.
And that’s supposed to be marked on the CUI standard as well. This is a big challenge for folks in the cloud. You’re supposed to be keeping the same standards as the government for their information.
Is my organization affected?
So is your organization affected? Well, the easy thing would just be to sit down and talk to the business people who hold the government contract and ask this question. Oftentimes, though, the business people don’t quite know. They’re scared to ask the program managers.
So maybe it’s easier for you as an IT person to bring up Office 365, start doing some content searches, see if you have any of this CUI in your systems today, now that you know the markings. So see if any of that is getting forwarded into your systems or saved in your systems. This is often a good place to start.
Are you doing business with the federal government?
Whether you’re doing business with the federal government indirectly or directly, you want to know if this is your requirement. Now, as an IT professional, not once have I had my customer actually flow down their requirements like they’re supposed to. I realized in the past couple of weeks, not once have they ever said, ‘You’ve got to have the same language in our contract as we have with the government.’ That’s one of the requirements that they’re supposed to have. And if you’re an IT person and then you’re outsourced into the cloud, you’re supposed to be putting those same things — like what I was showing you guys in the FAR clause — you’re supposed to be putting those exact same terms in your contracts to your cloud providers.
If you’re in this space and you need to know, another way you can know is by logging into SAM.gov. I think this is actually how we all end up with this problem in the first place. The business people are feverishly filling out this form, and all of these clauses are buried in there along with clauses that they’re not going to discriminate or do other illegal things. All of these things are buried in the contract and they’re just checking the boxes, agreeing with the terms and conditions and they’re overlooking it. But you can go right back to the source there, see if you have any DFARS clauses, see if you have any of these things in your contracts.
Department of Defense DFARS rule
So let’s get into the DoD. We saw the FARs, the Federal Acquisition Rules. Now let’s get into the DoD (Department of Defense) DFARS rule.
This one’s a little longer; I’m not going to put the whole thing up here. But basically it says, “We’re DOD, you need to meet NIST 800-171. And by the way, if you have a breach, you need to let us know in 72 hours.”
As somebody who is not the direct contract holder, it wasn’t clear to me if I needed to report a breach. And actually, I need to report the breach directly to the DoD. Even if you’re a sub of a sub of a sub, you should be reporting directly if you breach any CUI.
A lot of the attention around this space really got started with this Aerojet Rocketdyne case. Brian Markus was likely told by an executive, “You need to sign off that we’re doing all this stuff. We’ve got a big deadline, and we’re supposed to be doing this NIST 800-171. Just say that we’re doing all of it.”
And he said, “We’re not doing all of it, and I’m not signing off of it. And I’m sorry about your deadline.” I guess the executives just pushed it through on SAM.gov and checked the box saying that they were doing all of it.
Because it ended up that he was so disillusioned that he brought a [lawsuit under the] False Claims Act. This law dates back to the Civil War. The penalty is three times the contract value plus $11,000 per claim. Under the False Claims Act, a whistleblower can earn 30% of the contract value if the organization isn’t doing what they’re supposed to be doing. The case went to court, and Brian won. The executives were pushing it through.
The media attention really got the DoD thinking about the self-attestation everybody was doing. Executives are saying they’re doing all of this stuff, but they’re not. At the end of the day, no one is really doing this stuff.
So back in 2019, after having the NIST 800-171 out there for many years, they said, “This isn’t working. We’re going to have to send auditors in to verify that you are doing this stuff.” So that’s how we ended up with the CMMC certification.
CMMC is not in any of the contracts that the government’s pushing out there right now. They’re expecting it to be part of contracts starting in August 2024. Right now we’re in the rulemaking period, and it is expected to go into contracts in 2024.
But remember! Today, we’re already supposed to be doing this stuff in NIST 800-171. We’re already under the False Claims regime today. And really, it lines up pretty well with what we should be getting audited for in the future. So CMMC Level 2 winds up with NIST 800-171. And then if you’re just needing CMMC Level 1 for the FCI, that’s just 27 of the 110 controls.
Quick overview of the NIST 800-171 control families
So let’s do a very quick overview of some of the control families. I won’t go through every control, partially because they’re changing. But generally speaking, here’s the breakout, here’s the domains.
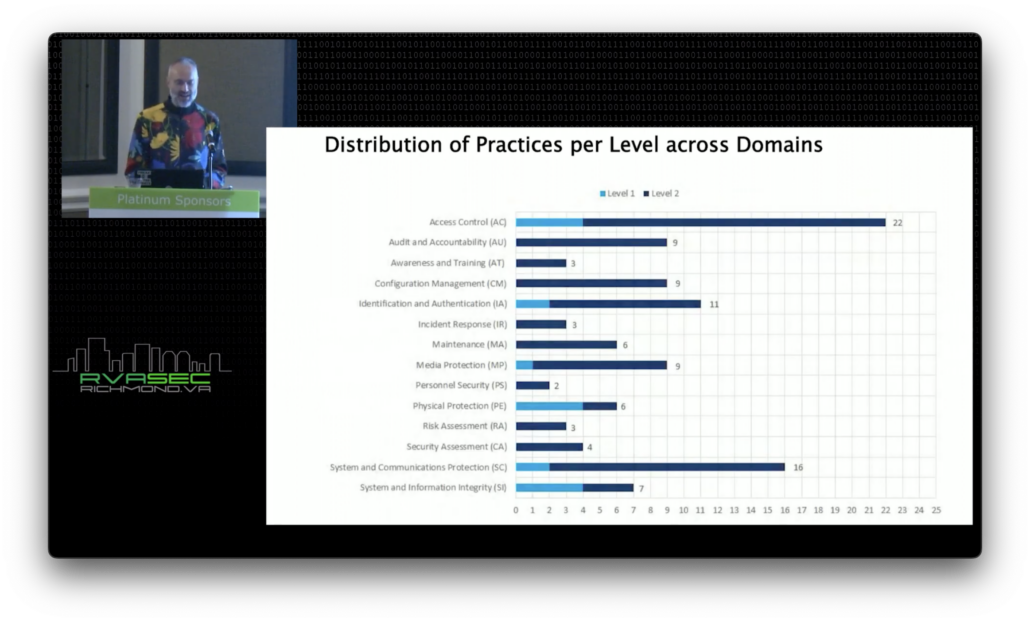
The ones that are marked in light blue, those are the Level 1 controls for just Federal Contract Information. But you can see here that there’s a LOT to do if you need to meet Level 2.
Now, this is something that I always like to show business leaders when we’re having discussions. This breakout shows the things that are administrative tasks. For years, the state of Virginia and their manufacturing extension was saying, “This is mostly a policies and procedures exercise.” Well, yeah, that’s pretty important, to have policies and procedures, governance.
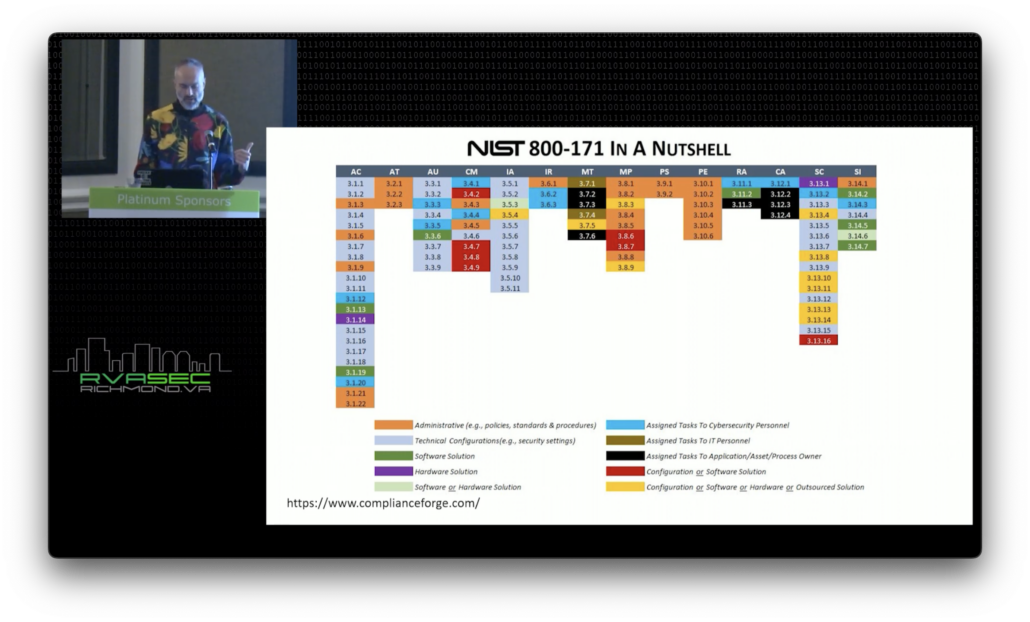
As you can see here, everything in orange has to be set up in policies and procedures. Everything in black needs to be assigned to business owners. These are all things we can’t do in IT. Brown and light blue items are assigned to IT on an ongoing basis. So if they’re expecting IT to just do this with existing staffing, with existing budgets, it’s not going to be achievable. This is not just a project, it’s not just buying a tool.
So how do I really like to look at these? Everything in NIST 800-171 really goes back to the dictionary, the giant bible of security controls, 800-53. In 800-53, they’re more broken down by stage as shown here. In 800-171, they usually have a paragraph that you read, and then you sort of have to deconstruct that paragraph to see all of the individual things. There are a lot of GRC tools that break them out like this, or if you go back to look at 800-53, you see them broken out. But each one of these tends to have multiple things that you have to do.
The thing that I’m trying to communicate here is that you’ve got to do all of the things to get the points for closing that particular category. And you have to do all of these things across all of the different systems that you have CUI stored in, processed in, or transmitted through. And you have to do that on the things that are securing those systems.
We’re going to talk a little bit about scoping here, but this is one way of really thinking about these domains and controls and individual objectives. There are 17 domains with 110 controls, but those controls are made up of 320 individual objectives and you have to meet all the objectives across every system that CUI touches.
What is your SPRS score?
A Supplier Performance Risk System (SPRS) score is the current way of self-attestation. You’re supposed to self-attest, and then if you’re not perfect, you’re supposed to be honest about it and upload your score. Now we’re seeing people that gave themselves a perfect score are getting audited. We’re also seeing people that have a pretty low score being warned that they need to get their score up or risk losing their DoD contract. So this SPRS score is starting to make an impact.
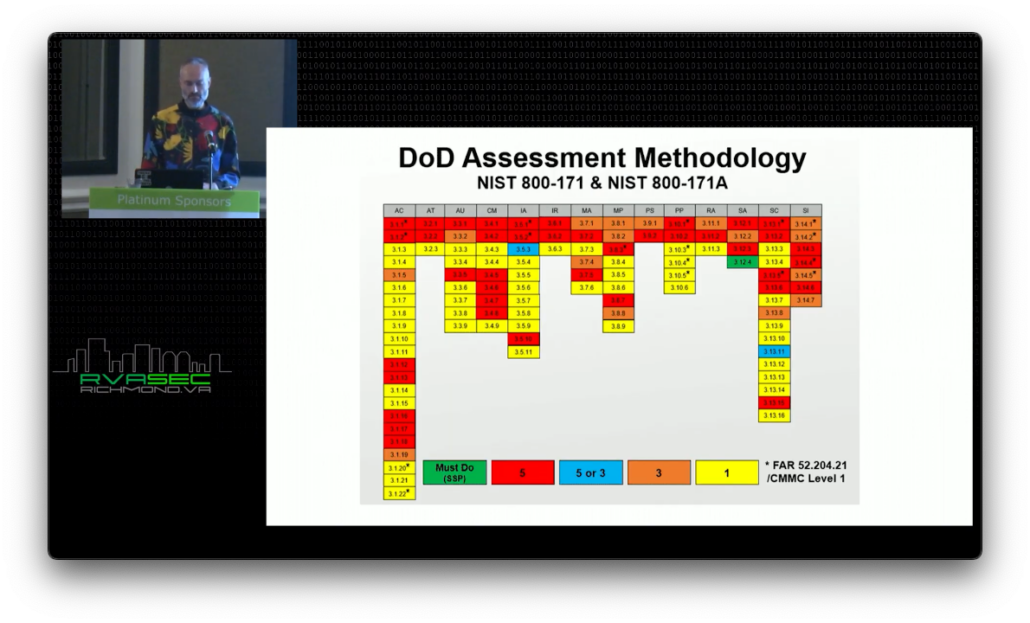
Under DoD’s current CUI scoring system, contractors start with a score of 110 and lose points for each applicable NIST SP 800-171 control that is not met by the contractor’s cybersecurity program. Contractors lose 1, 3, or 5 points for each unmet control based on the impact those controls have on the contractor’s cybersecurity program, with higher points associated with the more impactful controls.
Learn more at https://www.sprs.csd.disa.mil/
The scoring system is a nice way in IT to communicate with our bosses that something is an important control that we need money to implement. If you look at the whole matrix here, you kind of see the points break down across all of this. You see the red ones, the five-point ones. What’s that little green thing over there in the corner? That’s your System Security Plan. Of course, access control (AC) is at the head of the line, but the System Security Plan is really where we need to be starting. We’ll discuss that later.
So if you’re doing one of these SPRS score exercises, there’s a lot of good information out there about how to self-assess. If you’re going for Level 2, go over these two documents with someone in management to show what you have to go through. They’re actually pretty easy to read for non-technical people and not too big.
Self Assessment Guides
CMMC compliance strategies
Let’s talk about compliance strategies. The first one is to get management buy-in. And this is often a very interesting conversation because I find that for a lot of business leaders, it’s aspirational. You know, they’re doing business with the government today. They’re selling some socks, but they want to do more, so they want to get Level 2. So really getting on the same page with business leadership about what the actual goals are is really important here.
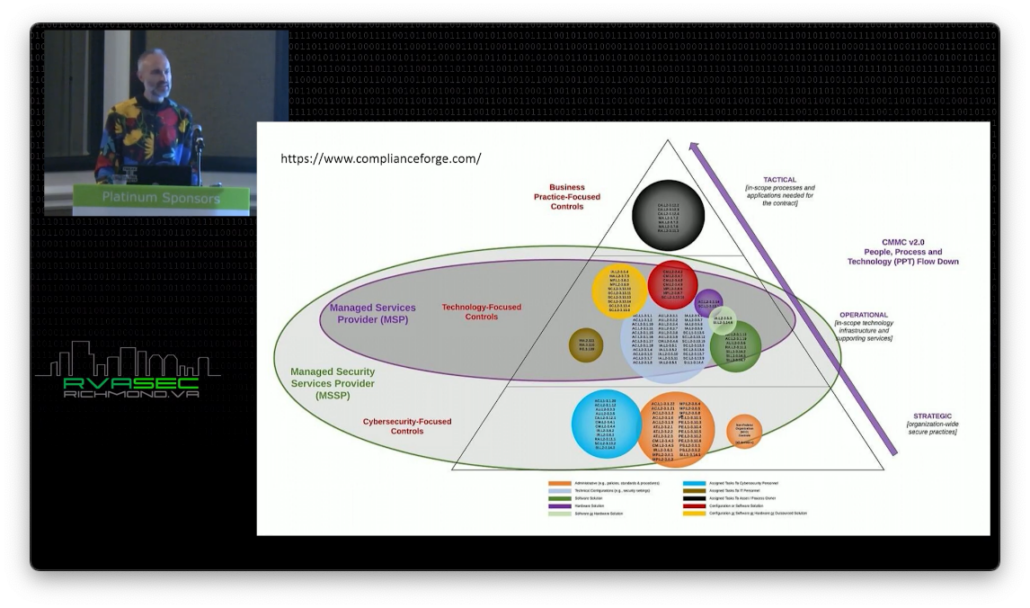
As you can see in this diagram, the black circle at the top is everything that needs to be coming down from the business, that the business owns, that they need to be communicating with IT. Out of the 110 controls, those are the things that they own. In many engagements I’ve been in as a compliance consultant that’s all been pushed on the IT guy. The business has the idea that this is a paper-pushing exercise, and IT is just going to go fix it.
So we need to reset expectations because, quite frankly, having good policies and procedures and good governance is the foundation of a lot of successful businesses. Many businesses scale this way. So this is a great opportunity. The government isn’t solving all of your business problems by making you do this standard, but it really is a good opportunity for people who may not have a background in doing good policies and procedures.
It’s really important to talk with your customers and suppliers to get them on the same page. Some businesses feel that they can’t tell the government what to do. But you can give them instructions on how to talk with you securely; that is within your control. Setting and upholding those standards will make it much easier for IT to keep you compliant.
So what is this not going to solve for the business? 800-171 is a confidentiality requirement. The government is whispering their secrets in your ear, and they want you to keep it secret at the same level that they were. It’s confidentiality.
It’s not going to help your business recover from a disaster. The government doesn’t care if you go out of business. You’re way down on their supply chain. This is confidentiality only. And I think that’s another thing we need to really drive home to business leaders, is this is not solving all of the problems in IT. There’s still other things that we have to be doing in IT and security than just this. So ISO has much more about business continuity within their framework.
If you want to learn more about the 800-53 framework, which is sort of the master dictionary of all of this stuff, The Cyber AB website has a good May 2023 Town Hall that goes into the relationship between the two frameworks.
All right, so let’s talk a little bit about scoping. We have to be storing, processing, or transmitting CUI. We probably have multiple systems that are doing that, and then we have security protection assets. These are the things that are protecting the systems that are storing, processing, or transmitting CUI. Those are the systems that we primarily need to protect.
Out of scope would be things that aren’t doing those things. Today, the Internet of Things (IOT) goes into that space. That’s a little concerning to me, but that’s another conversation. Contract risk managed assets are computers next to the computer that’s storing, managing, or processing CUI; they are supposedly not storing, processing, or transmitting CUI. You still have to inventory all of those things, and in IT we want to be segmenting those things. We also want to have business processes, our policies and procedures, that defines that we have that segmentation in place for our users to follow. But this is a big opportunity to maybe reduce the scope of an audit and reduce the burdens on everyone if we correctly categorize contract risk managed assets.
So let’s think about this. In the real physical world, if we’re defining the boundaries of our systems and our System Security Plan then we have to have a sign on the door when we’re processing CUI. There’s a lot of people working from home today. There are some business conversations that have to happen: not just how will we handle this in IT, but in the real world, too. We have to get all of that in alignment.
Engage your customers and suppliers about CUI
- Talk to your program manager or prime about CUI shared
- Give your program manager or prime instructions on how to securely communicate with you
- Define the flow of CUI so you have your scope
- Flow down your FAR/DFAR requirements to your sub-contractors
- Cloud providers need to be FedRAMP Moderate Equivalent
CMMC assessment process
So the auditors are coming. How is that going to all roll out? Well, IT’s grown up in a period of profound deregulation, so they’re not doing what the building inspection department has done; they’re not hiring auditors. This is going to be a big costly exercise. It’s private sector, not taxpayer funded.
The DoD has stood up a nonprofit, The Cyber AB, which is training implementers. I’m an implementer, a coach for implementing these standards. They’re also training auditors. You can’t play both roles [for the same client]. If you’re an auditor, you can’t be coaching the people you’re auditing, so you have that separation of duties.
But the auditors are the C3PAOs, and there’s 42 of those in the country right now, with a wait list of about 400.
I’ve also done my training for the Certified CMMC Professional (CCP), which would be to serve on an audit team. I wanted to see what the audit teams were getting trained to do, so that was helpful as a coach. I know what the audit teams are going to be inspecting.
You’re going to have a lead auditor. You’re going to have some helpers. These audits are going to be expensive.
How often will you assess your systems? Every three years it seems like (the rulemaking is still taking place). It’s not really certain how much self-attestation will be taking place in the future, but it seems like everybody is getting on board with having some third-party audits.
How often will you assess?
Level 1
- Federal Contract Information (FCI)
- Annual self-assessment
- Update your score in SPRS system
Level 2
- CUI critical to national security
- C3PAO (paid auditor) every three years
Level 3
- Government-led assessments every three years for high-priority defense programs
10 steps to achieving CMMC Level 2
- Form implementation team
- Identify CMMC level
- Define compliance scope
- Create gap analysis
- Create gap remediation, w/CMMC Registered Practitioner if needed (1-2 years)
- Source a СЗРАО (CMMC auditor)
- Be assessed by C3PAO
- Submit report to DoD.
- If at least 80% of the criteria are met, use the 180 days allowed to remedy Plan of Action and Milestones (POA&M) to 100%
- CMMC L2 certificate issued by The Cyber AB
These are big programs; it takes a couple of years [to achieve certification]. Yet most business executives I talk to seem to think that this can just be done in a couple of months. So that’s a big disconnect right now.
What’s new with NIST 800-171 in 2023?
In May 2023, a new draft — NIST 800-171 Rev. 3 Draft — was released. Basically they took out 27 controls, merged them into other areas, and added in 27 more. But honestly, they are things that we were all supposed to be doing anyway, like flowing down the contractual requirements and having policies and procedures. If you look carefully, those were assumed in the previous versions. Now they’re no longer assumed.
Third-party audit requirement
But I think what’s interesting about this is that now NIST is saying we’re going to require a third-party audit. So CMMC is a DoD program, but NIST affects many other government agencies. A lot of private industry recognizes the standard. So I see this more as becoming a building code for having some privacy requirements in our businesses.
Even though it’s only 75% consistent with the earliest revisions back there in 2016 or something, I didn’t really find anything really shocking in this latest version.
Organizationally defined parameters
One of the things that seemed like it took a more prevalent role in this latest revision was organizationally defined parameters. Up to now, people usually think these are things that their organization needs to define. Instead, it seems like they will flow down from your government contract, and the ones that the government doesn’t define will be left up to you. For example, if you’re not dealing with really highly sensitive CUI, the government may choose not to define it. I really hope that they leave some latitude.
Overall, this latest revision turned assumptions into requirements and shuffled some things around. There is now more clarity and less assumptions, with the exception of those organizationally defined parameters.
Here’s the breakdown that my research came with what was going in and out, or that are no longer assumed but required. At the end of the day, these are not crazy requirements. You’re either already doing them or it’s not too difficult to start.
ODP Facts
65 controls have 107 Organizational Defined Parameters (ODP)
ODP can be set by the following:
- National Archives
- DoD
- International Traffic in Arms Regulations (ITAR) – Department of State
- You the Contractor
Breakdown of changes
Were NCO in 53r4, now Controlled Unclassified Information (CUI) in 53г5:
- AC-2(3) – 3.1.1 Disable Accounts
- AU-11 – 3.3.3 Audit Record Retention
- SI-8 – 3.14.8 Spam Protection
Were CUI in 53r4, now NCO in 53r5:
- CP-9 – 3.8.9 System Backup
- MA-2 – 3.7.1 Maintenance
Were Non-Federal Organization (NFO) in 53r4, now CUI in 53r5:
- *-1 (16 total) – Policies and procedure 1. CA-2(1) – 3.12.5 Independent Assessment
- CA-3 – 3.12.6 Information Exchange
- CA-9 – 3.13.7 Internal System Connections
- CM-2(7) – 3.4.12 High Risk Area Configurations
- IR-8 – 3.6.1 IR Plan
- PL-4 – 3.15.3 Rules of Behavior
- PS-7 – 3.9.3 External Pers. Sec
- RA-5(2) – 3.11.2 Vuln Scan
- SA-9 – 3.16.3 Ext. Sys. Services
- SC-7(3) – 3.13.18 System Access Point
So a lot of this is kind of looking at sausage making. What I’ve realized is that this being a government program, there being a reasonable amount of transparency around this, that you can really get caught up in the sausage making. But at the end of the day, a lot of these things are things that IT has really been begging management to do for a long time anyway.
If you don’t like the changes, you still have until July 14 to push back on NIST and say, “Is this really required?” But if you do want to look at the sausage making, follow Robert Metzger on LinkedIn. And keep an eye on the 2024 Go Live date, because it may very well be that your CMMC certification is going to be going up against this revision three. That seems to be the best indication today about where they want things to go.
Tips and tricks for achieving CMMC compliance
Start with system boundaries, not access control
Don’t start with access control. When you have a meeting with the business leaders and you start at AC, it goes very wrong. Instead, try to work with them to understand the boundaries of the system.
Oftentimes, business leaders don’t have good change management systems. But there will probably be a lot of changes to make. It’s not just an IT exercise to get everybody to do things securely.
For example, I work with a lot of organizations that are 25 to 100 employees. If they don’t have some good frameworks around managing change, I recommend that the business leaders read Traction by Gino Wickman. It has an operating system for a business, how that business can work, and manage change, including policies and procedures. This is a great book that drives home the value of policies and procedures as an opportunity to scale and grow and get everybody on the same page without overwhelming them — because it is going to be a big change. I’ve seen this be very helpful to businesses.
Talk to legal
You also want to work with your legal team, because you need to make sure your contract requirements flow down. This is a federal requirement. Whether your prime is doing the right thing in their contract with you or not, you’re still getting the federal government’s information. And that’s still putting you in a liable situation, even if the person giving it to you isn’t doing the right thing. You will want some counsel. (I found great lawyers on Upwork, by the way.)
Use a GRC tool
You may also want to consider a governance, risk, and compliance (GRC) tool. A GRC tool helps IT staff to delegate tasks to management and vendors. If you’re outsourcing some IT functions, it helps you delegate and manage projects.
I use FutureFeed because I found it to be the best and easiest to use. One nice thing is that when NIST revisions happen, the application automatically pulls in those changes. It gets you out of Excel hell.
Why we use FutureFeed
During our consulting engagements, we were seeing that a lot of time was being lost to version control, to managing documents and the flow of information. To solve that problem, we looked at probably a dozen tools, and spent a substantial amount of time before selecting FutureFeed as the one that we wanted to use.
What we like about FutureFeed is that it engages the business team first. It does a great job of onboarding folks: it has the business leaders put in their CAGE codes and define the types of CUI they have, and then it involves IT once the business leaders are engaged. It has a matrix which shows who in the business is responsible for various controls. It has templates for policies and procedures and makes it easy to document them. It’s also based right out of Maryland.
Get training
There’s tons of training available. The Cyber AB has training. I went through the Registered Practitioner training. It was probably eight hours. I did it over maybe two weekends. It wasn’t bad. That’s the entry-level coaching role.
There’s lots of free training out there on how to handle CUI.
There’s this Project Spectrum. If your business is working on policies and procedures and you want to have somebody review your plans, you can send it over to Project Spectrum and you can get some coaching on that.
For a long time, the federal government has issued notices around security threats.
There’s even services that you can subscribe to to talk about threat actors, or how people are getting into your networks. They’re going to be giving that information away for free through the Defense Industrial Base (DIB) Cybersecurity (CS) Program so you can get some coaching around security.
There’s a lot of good resources out there in the training space.
Costs and pitfalls of seeking CMMC compliance
Let’s talk about costs and pitfalls. A CMMC Level 2 audit will cost $25,000 to $50,000. You don’t want to go into this without getting the business in alignment. You don’t want to go in this without having all of your ducks in a row. If you pay for an audit and fail, you get 180 days to remediate—180 days to fix it all.
I made a list of about $2,000 a month worth of tooling that I see commonly missing from a lot of small businesses. Then add a coach like myself, starting at $750 a month to provide some coaching services around compliance.
Another pitfall is keeping an eye on the unknowns, like the overuse of the CUI category and contracts or the quality of the assessment workforce.
I was in that assessor training. It seemed like one-third of the people there had the right background to connect with small businesses. That concerns me—are there going to be rubber-stamped assessments?
The biggest pitfall, though, is aligning all of the requirements.
Compliance versus security. Sometimes the tendency is to focus on one or the other, but we need to allocate the resources for both. I was working with a recent customer who felt that because we need to be audit-ready, we have to push a security project down the road. But CMMC compliance needs to be part of your business-IT strategy.
The ITAR question: What level of FedRAMP is needed for our cloud? This is a big one. A lot of people are not really clear on what type of information they have, but it will absolutely affect the level of FedRAMP compliance you need, and your costs for Microsoft 365, AWS, or any other tool that you use. Make sure to have those conversations with the business leads.
Putting everybody in Microsoft 365 GCC High when they don’t need to be is very costly. GCC High licenses are 50% to 70% more expensive than GCC licenses and you must pay for a full year upfront. I was working with an organization where they had 110 employees, maybe five dealt with ITAR, and they were all on GCC High. That is a big, costly pitfall. You can avoid this by segmenting the organization or using a tool like PreVeil.
Going another way, using too many different systems can be a costly pitfall. Avoiding these pitfalls requires conversations with business leadership, which is often what is lacking.
CMMC Level 2 compliance costs
- GRC tool: $325/month
- Microsoft 365 GCC High: $52/user/month
- MSSP tooling: $50 to $70/user/month
- SIEM and event logging
- Device management
- Device patching
- AV/EDR
- Whitelist tooling
- Multi-factor authentication (MFA)
- Encryption
- Security training: $10/month
- CMMC consulting: $750 to $1,500/month
- Level 2 audit: $25,000 to $50,000
Customer experiences in becoming CMMC compliant
Here are some folks that we’ve helped on their compliance journeys:
TekFusion Global
- Website: www.tekfusioninc.com
- Contact: Dave Wolons (LinkedIn)
MC3 Solutions, LLC
- Website: mc3solutionsva.com
- Contact: Cindy Collins (LinkedIn)
At the end of the day, I don’t think the CMMC compliance program is going to build the IT Monticello of my dreams, but it may give us a perfectly acceptable, secure little house that’s more reliable, less chaotic, more engaged with business than what we had going into this. That’s my hope.
Next Steps
When you have the right people working together, you can implement systems and processes that actively help you reach your business goals. We sometimes call this IT maturity. But for many organizations, something is off when it comes to their partnerships, strategy, systems, and settings. How can you know what’s working well and where you have room for improvement? Start by taking our free IT Maturity Self-Assessment. You’ll walk away with some pointers and, if you want, a free appointment to discuss your results.
Take the IT Maturity Assessment

Is your business ready to weather changes, including employee turnover? Find out by taking our IT maturity assessment.
You’ll get personalized action items that you can use to make improvements right away. Plus, you’ll have the opportunity to book a FREE IT strategy session to get even more insights into your IT needs.

Industries
Locations
Waynesboro, VA
Corporate HQ
215 Fifth St.
Waynesboro, VA 22980
Sales: 540-217-6261
Service: 540-885-3129
Accounting: 540-217-6260
Fax: 703-935-2665
Washington D.C.
1126 11th ST. NW
Suite 603
Washington, DC 20001-4366
Sales: 202-888-2770
Service: 866-692-9082
VA DCJS # 11-6604
Locations
Harrisonburg, VA
45 Newman Ave.
Harrisonburg, VA 22801
Sales: 540-569-3465
Service: 866-692-9082
Richmond, VA
3026A W. Cary St.
Richmond, VA 23221
Sales: 804-729-8835
Service: 866-692-9082
